010Editor简介
010Editor是一款文本编辑工具,能够编辑文本文件、XML、Unicode和UTF-8、C/C++源码等。
无限的撤销和强大的编辑和脚本工具。
巨大的文件支持(50GB+)。
010Editor是一款优秀的十六进制/文本编辑工具,其内置的模板功能对于学习文件格式有极大的帮助。010中包含着许多复杂的工具,用于分析和编辑二进制文件。并且支持脚本,便于更好的自定义您的编辑习惯。
当然,010Editor是一款收费软件,本次秉承着学习的想法对其实现进行分析。
逆向初步分析
已知条件:Qt5程序
思路:使用OD动态调试
- 程序有随机基址,去掉随机基址拖进OD
- 寻找关键函数和字符串并下断点
- 自动分析后逆向跳转至关键比较部分
- 寻找比较过程中的判断位置以及未知用处的函数调用
- 修改关键部分代码(暴力破解)
- 逆向分析算法,写出注册机
在未知Qt函数的情况下,通过对User32.dll模块的CreateWindowA/W函数下断点,然后进行栈回溯,找到在主模块中调用的Qt中封装winapi的函数,即可断下程序的弹窗位置
对于未知API的情况,也可以通过字符串查找找到关键调用部分
暴力破解
对CreateWindowA/W下断,找到主模块中调用的call,并对每个call下断,逐个分析
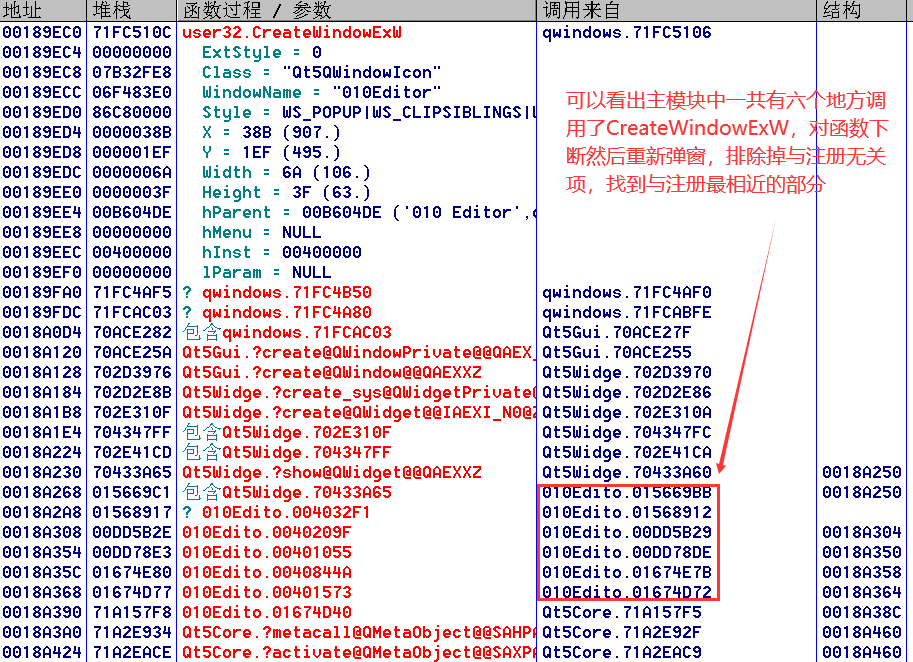
找到关键的函数调用部分
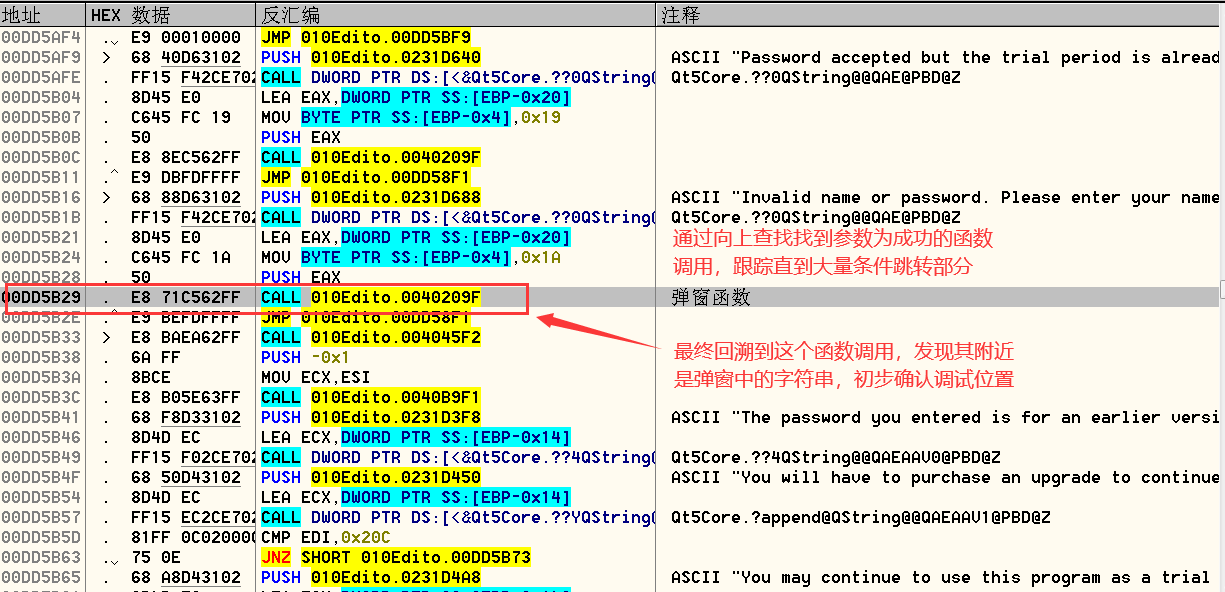
逆向向上查找,最终定位到关键位置
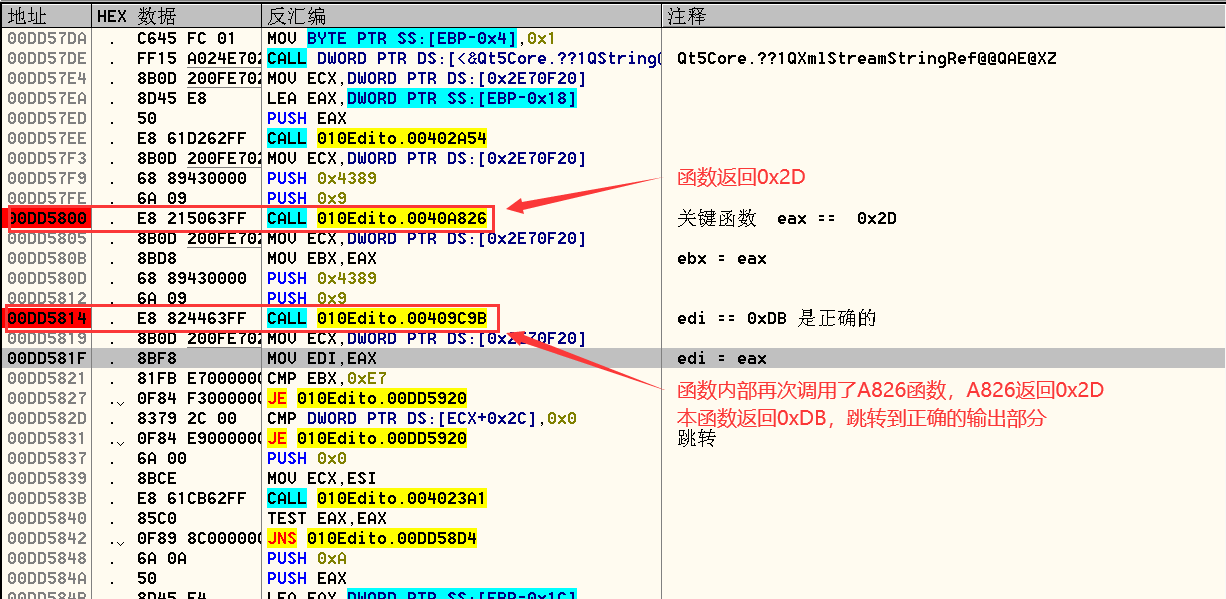
如果想要通过暴力破解的方式完成对软件的破解,只需要让0x0040A826函数始终返回0x2D即可
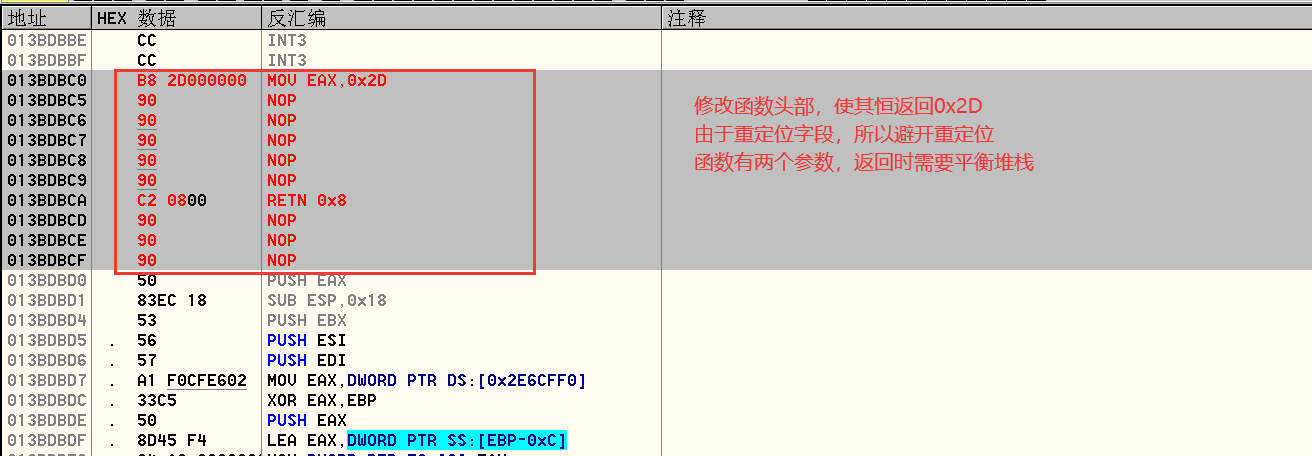
至此,我们便完成了对010Editor的暴力破解
校验部分算法分析
进行算法分析首先要定位到校验部分
通过逆向跟踪jcc指令定位到相邻的两个call处
单步跟踪进入到第一个call中
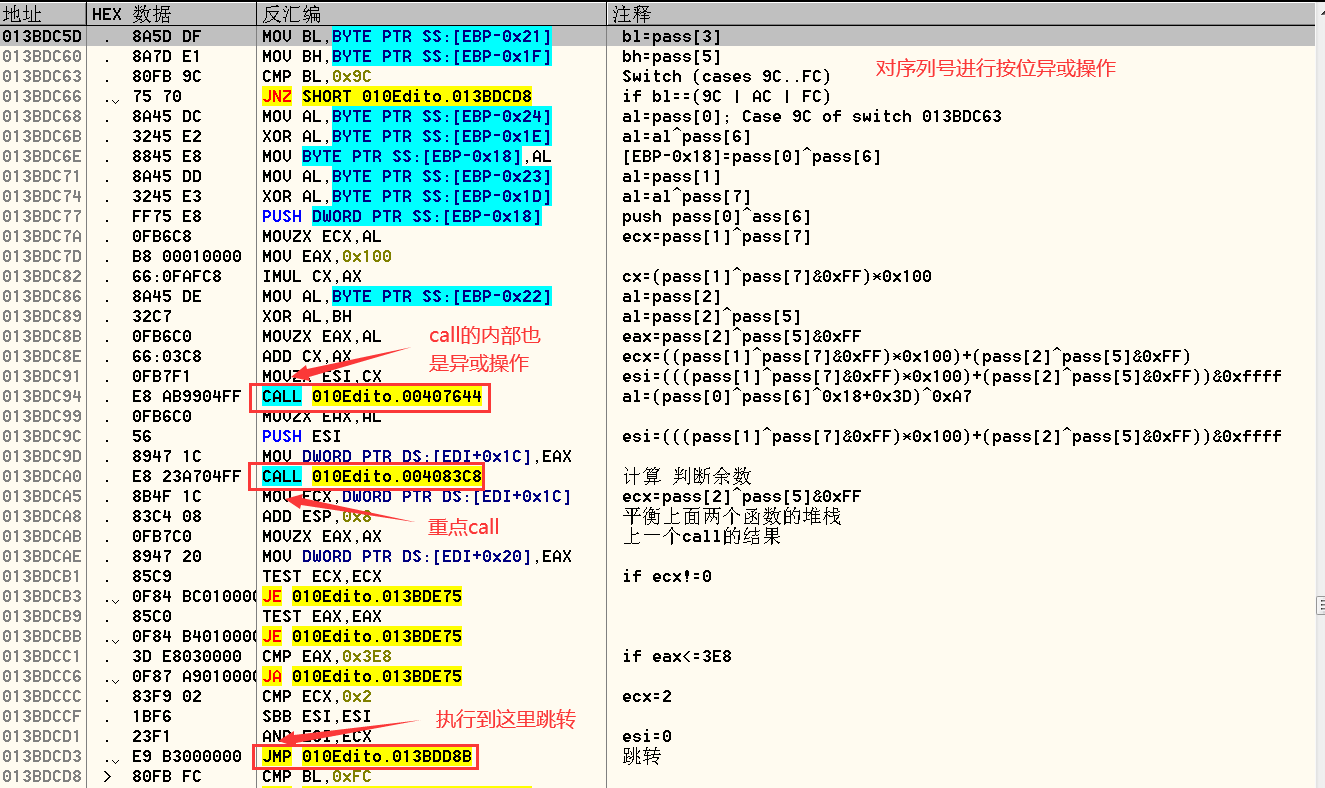
分析后发现在0x0040A826函数中存在着大量的异或操作,并且有两个函数调用。跟进第一个函数
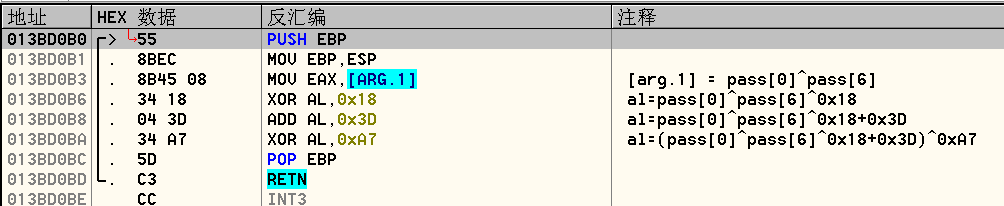
函数中同样是异或操作,然后将操作后的结果返回。再此跟进第二个call
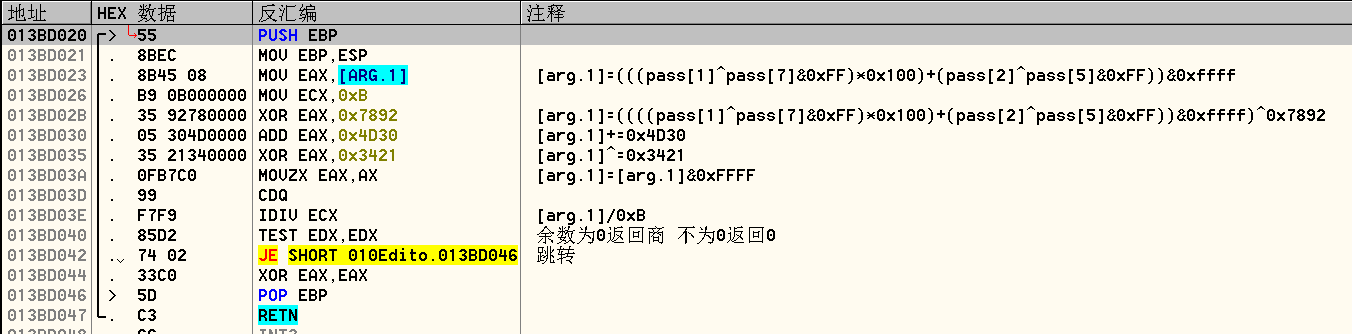
同样是对参数进行异或操作,完成异或后,将结果与0xB做除法,余数为零则返回商,不为零则返回零,并将余数保存在EDX寄存器中
跳转到下面比较用户名部分
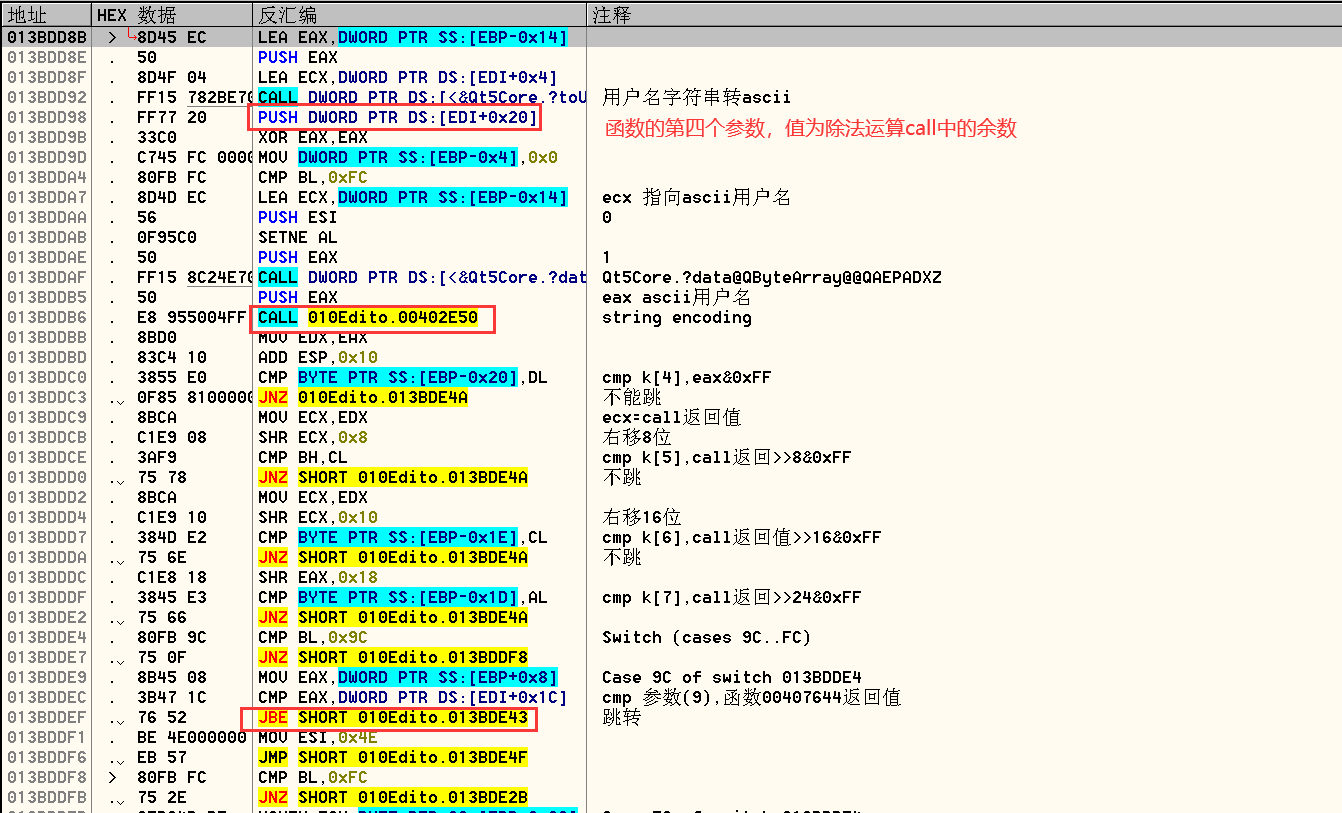
用户名传入了一个未知函数,其返回值通过移位的方式与序列号进行比较。猜测此函数是计算用户名特征值的函数,call后面的ADD ESP,0x10说明了函数有四个参数,cdecl调用约定。跟进函数发现内部是一个与校验盘运算求出特征值的函数,使用IDA插件还原源代码
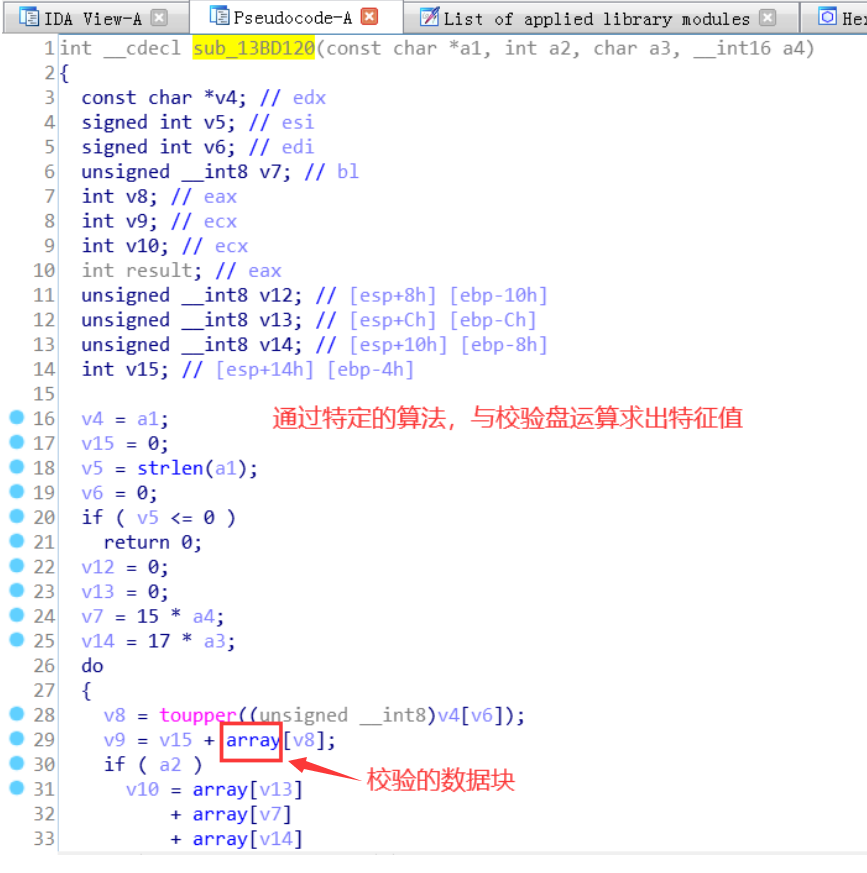
至此,我们便完成了对010Editor的验证算法的初步分析
编写注册机
了解了验证算法之后,可以通过分析出来的结果编写注册机
现已知程序现对序列号进行一定的判断,再通过特殊的算法使用用户名算出四字节的校验值,最后用校验值与输入的序列号进行比较,判断是否正确
1 | srand(time(0)); |
通过随机数的方式计算出了一个能够运行到验证用户名的部分,将用户名生出的算法抠出来,再dump出校验盘,将函数加入到我们的代码中去,最终的代码为
1 |
|
至此,010Editor的注册机也就完成了